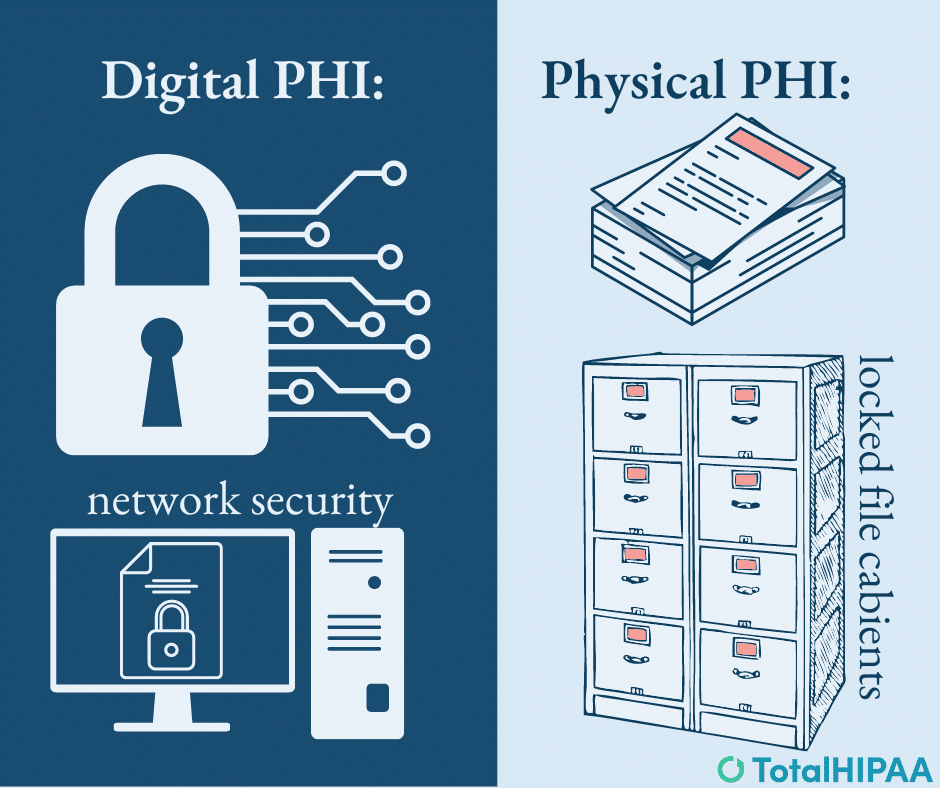
Security is crucial for hospitals and doctors’ offices to protect sensitive patient information. In this blog post, we’ll explore the significance of physical and network security.

The Impact of Physical Security
Imagine walking into a clean and well-organized doctor’s office. The waiting area is tidy, patient files are securely stored, and only authorized personnel have access to patient areas. In such an environment, patients immediately feel a sense of trust and professionalism. They know their PHI is handled with care, enhancing their confidence in the healthcare provider and the confidentiality of their personal information.
On the other hand, a messy and disorganized doctor’s office raises concerns in patients’ minds. Papers are strewn about, files are misplaced, and anyone can access sensitive information. Patients may question the security practices in place and worry about their PHI falling into the wrong hands. A cluttered environment compromises patient privacy, potentially eroding trust and leaving patients feeling uneasy.
Extending Security to the Digital Realm
In today’s digital age, protecting patient information goes beyond physical security. Anyone working with PHI must prioritize network security to safeguard electronic health records (EHRs) and other digital systems. Network security measures help defend against unauthorized access, data breaches, and the compromise of sensitive medical data.
Introducing Iceberg Cyber
To effectively address network vulnerabilities and strengthen security measures, healthcare institutions can rely on industry experts like Iceberg Cyber. Iceberg Cyber specializes in network security solutions, including vulnerability scanning, to identify and mitigate potential risks. We are excited to announce that we will be hosting a webinar on July 19th at 2:00pm featuring the founder of Iceberg Cyber. This webinar will delve deeper into the importance of security for hospitals and doctors’ offices, focusing on network vulnerabilities and best practices for safeguarding patient information. Mark your calendars and join us to gain valuable insights from a leading expert in the field.

The Benefits of Vulnerability Scanning
Working with Iceberg Cyber helps anyone who stores sensitive data online and in private networks identify and fix vulnerabilities. Regular vulnerability scanning reduces the risk of data breaches and ensures compliance with regulations like HIPAA, which protects patient privacy. Iceberg Cyber partners with Total HIPAA, a comprehensive compliance solution.
Prioritizing security is essential for creating a trusted healthcare environment. Total HIPAA specializes in HIPAA compliance services, helping businesses adhere to HIPAA guidelines and protect sensitive data. Our experts ensure your organization remains compliant with HIPAA regulations, meaning you can focus on your core operations while we handle HIPAA’s significance and guidelines. Book a clarity call with Total HIPAA today for a comprehensive compliance solutions tailored to your needs.