THE TOTAL HIPAA
Resource Library
Are Your Clients HIPAA Compliant?
This article and infographic was originally published by the Maurice A. Deane School of Law at Hofstra ...

Employer Group Breach Woes
Discover recent employer group breaches that exposed employees' Protected Health Information (PHI), including ...

Penetration Testing: Adding Value to Your Security Posture
As you strive to make HIPAA compliance one of the most important aspects of your organization, you likely have ...

A Look Into an HHS OCR Desk Audit
Since 2016, the Office for Civil Rights (OCR) in the Department of Health and Human Services (HHS) has been ...
Preparing For Every Disaster
While recovery from Hurricane Harvey is under way and evacuations begin in Florida as Irma approaches, Total HIPAA ...

Smishing – The Next Cyber Threat
It seems like cyber attackers and scammers have been making headlines more and more lately as they’re finding ...

A Year In the Life of HIPAA
Data breaches are on the rise, and your awareness about becoming and staying HIPAA compliant likely are, too. In ...

A History of HIPAA: 8 Things You Should Know
The Health Insurance Portability and Accountability Act (HIPAA) was enacted in 1996 to protect American families ...

A Data Breach Affects Your Wallet – and Your Reputation
When you prepare for HIPAA compliance, you may not immediately think about the possibility of a data breach and ...
The Ins and Outs of Risk Management
Risk Assessment and Risk Management
A Risk Assessment1 is a first step in protecting your organization, but it ...
My Business Just Experienced a Cyber-Attack!
What's New?
Health and Human Services, Office for Civil Rights (HHS OCR) released a cybersecurity checklist and ...

5 Common HIPAA Mistakes
Now more than ever, HIPAA compliance is a must.
It’s hard to believe, but HIPAA errors found to be violations can ...
HIPAA Compliance Will Stop Ransomware’s Damage
On average, there have been 4,000 daily ransomware attacks since early 2016, an increase of 300% from the 1,000 ...
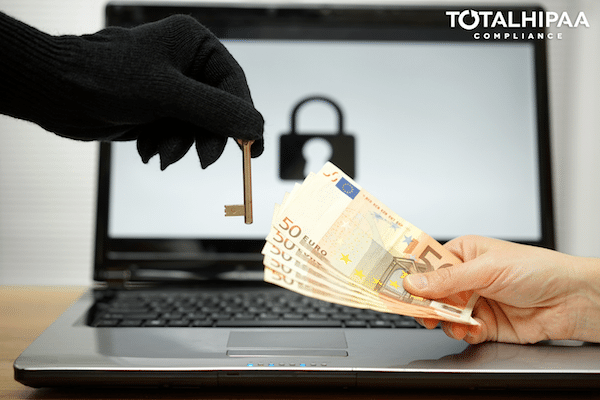
WannaCry Ransomware Protection with HIPAA
WannaCry, WannaCrypt, Wana Decryptor or WCry, whatever it is called, ransomware has been spreading through over ...

Creating and Managing Passwords
How many times a day do you access applications or websites that require passwords? The temptation is to make ...

Malicious Social Engineering and HIPAA
Spam accounts for 65% of the total volume of global internet email traffic according to Cisco’s 2017 Annual ...
HIPAA Violations Every Day and Every Size
We frequently get questions about whether or not an event is a HIPAA violation. Some of the events are hazy, ...

Navigating HIPAA and State-Specific Medical Records Retention Requirements
The Health Insurance Portability and Accountability Act (HIPAA) mandates that Covered Entities and Business ...

Auditing Business Associates
Have you Audited your HIPAA Business Associates?
This question comes up frequently when we are working on HIPAA ...

Implementing HIPAA is More Than Meeting Government Regulations
Recently, I was on a vacation in Germany, and as I visited several medieval cities, I had two thoughts. First, ...
No results found.
Take control of your compliance.

