So you’ve decided to go self-funded* for the employee health plan at your company. You may have been wondering if this means you’ll have to do something about “HIPAA”. If that didn’t cross your mind, hopefully you have a benefits manager or an insurance agent who you are working with who is aware. In any case, staff at your company will have access to PHI and under ERISA, your company is the custodian of the health plan. As the custodian, you are required to protect your employees by protecting their PHI. This means you need to be HIPAA compliant as an employer. HIPAA compliance means having a plan.
Here are three common pitfalls to look out for in your HIPAA Compliance Plan:
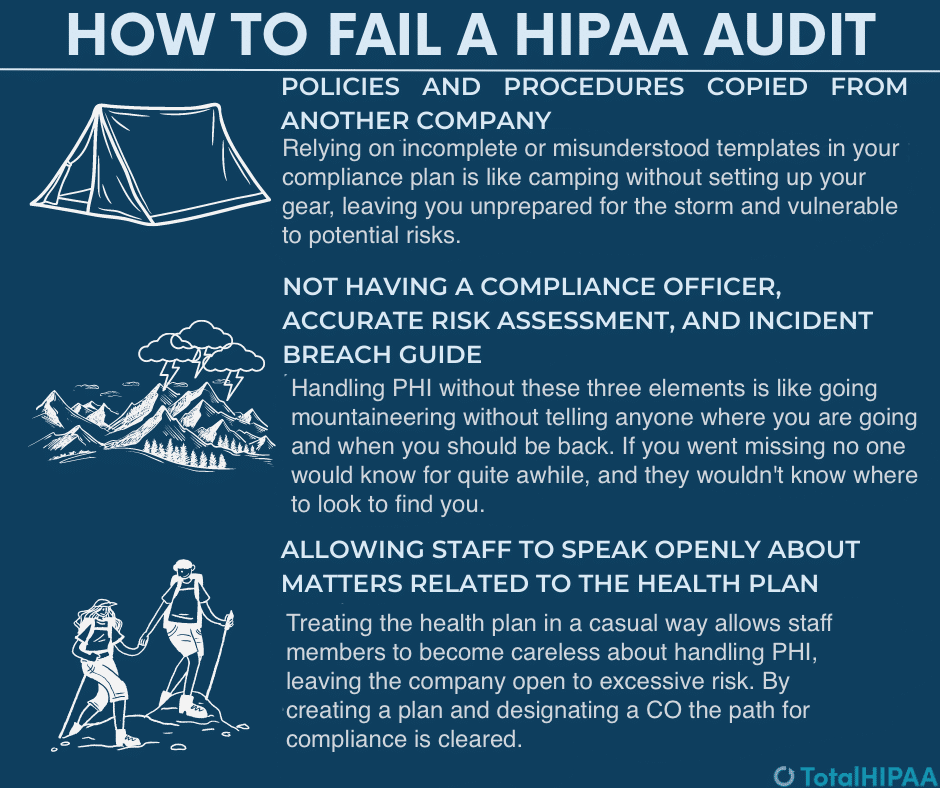
1. Policies and procedures copied from another company
Your team didn’t create these policies, and from an auditor’s standpoint, these are just a placeholder for what actually happens. Documented policies are often dry and therefore not read and understood by all the staff that are affected by them. The documents that make up your compliance plan are required to be customized to your business, otherwise, it’s likely that your staff won’t be found to be following the policies, should a surprise inspection happen.
Using a template or a document that isn’t fully accurate or fully understood in your compliance plan is like going camping with a car full of gear but never setting it up. Once the storm hits, it’s not as easy to set up an entire camp, whereas having everything set up and in place before the wind picks up allows you to see what vulnerabilities exist so you can make some final adjustments and then wait for the storm to pass under shelter.
2. Not having a Compliance Officer, accurate Risk Assessment, and Incident Breach Guide
Some departments consider themselves to be HIPAA compliant just by knowing and following their own guidelines regarding PHI. Or perhaps since training is the only annual requirement, you might be under the impression that training your staff is enough. Unfortunately, since HIPAA has been around so long, its modern interpretation isn’t taken into account. Most staff members aren’t thinking about HIPAA when they check their email and go about their regular tasks.
Knowing the difference between HIPAA compliance and HIPAA know-how is key. Hiring someone with experience in HIPAA is certainly helpful, but it doesn’t mean they will know how to create the documents your company is expected to have. It’s more likely they know how to carry out the policies and procedures from a different company. Since they weren’t part of the process of creating those policies, they may be under the impression that everything they did at that company was standard HIPAA protocol and that by doing the same thing for you, your company will be HIPAA compliant. Not so.
Imagine if a hacker decided to target the PHI in your company’s health plan and they sent out a phishing email to a handful of staff members with your CPO’s name and the company’s domain name but with two “r”s instead of an “m.” The email could have a message like “click here to confirm your benefits enrollment,” which when clicked by an employee installs malware or asks for login information. If you don’t have someone designated as your Compliance Officer, an individual the entire staff knows they can contact in the case of an incident, this unsuspecting employee will likely do nothing. In this case, your company will remain unaware of the breach and any number of things could happen with the data that is accessed. It could be leveraged in a ransomware attack, or it could be stored for use at a later date.
The best thing to do is to designate a leader at your company to be the Compliance Officer and make them part of the process of filling out a Risk Assessment and finalizing an Incident Breach Guide. Our HIPAA Prime customers go through this process and are well-equipped to handle an incident- making sure it doesn’t become a breach. By creating a document that outlines what to do if PHI is accessed by the wrong party, you can save a lot of time tracking down the hacker, denying access, and analyzing logs to see what, if anything, was downloaded.
Not having any of those three required elements is like going mountaineering alone without telling anyone where you are going. Sure, it can be beautiful and fun on a day with no clouds, but the closer you get to the top the more likely a storm becomes. Once you are at that level of exposure, you are risking a lot more than any normal walk in the park. Therefore, you need to make sure people know where you are going, and what to do if you don’t come home by a certain time. If you don’t take precautionary steps, no one will know you’ve been missing until much more time has passed, and once they do realize something is amiss, they won’t know where to look.
3. Allowing staff to speak openly about matters related to the health plan
Without a comprehensive approach to HIPAA compliance, you won’t create a culture of awareness around PHI. Not only does this increase the risk of a cyber attack being successful, it also increases the chances of someone knowing something about their co-worker that said coworker considers private. If health information about an individual, such as pregnancy status, COVID test results or pending surgery become common knowledge, that individual would likely feel that their privacy was violated. If the company is required to be HIPAA compliant and this happens, they are considered in violation of the law.
Even if the worst thing to happen was the information getting out and nobody filed a complaint, there is no telling how many people would see that as a violation of trust, and there’s no predicting who they would speak openly to about it. The best thing to do is make sure everyone with access to PHI is trained on HIPAA, given a Notice of Privacy Practice so they know what to expect, and that the Compliance Officer is always the first person to be contacted if someone suspects their information got out.
Conclusion
To sum it up, partnering with Total HIPAA can help make sure an incident or breach is less likely to happen and that if one does occur and an investigation ensues, that your company passes an audit with flying colors. We have developed a four-step process that ensures compliance for all of our clients through becoming aware of the risks and creating a plan to mitigate them. Our experts guide your team through the process so that they receive training and participate in creating the plan that will keep your company safe. Once we’ve created the plan we remain on your team to keep your company on track so your staff can focus on doing their job well- not endlessly researching how HIPAA is being interpreted and enforced.
Please reach out to our sales team by booking a demo through the Get Started page. We’d be happy to take 15 minutes to talk about your current approach and how it could be improved by working with us at Total HIPAA.
If you feel confident that none of these potential mistakes apply to your company but you still don’t feel 100% confident that you are HIPAA compliant, consider using Vulnerability Scanning to take a closer look. We have a webinar coming up with Iceberg Cyber where we will discuss this topic. Please feel free register for the webinar here, and once it’s passed sign up to view it on our website here.
*self-funded as well as level-funded employee health plans serving over 50 lives are considered covered entities due to this ruling: Section 45 CFR 160.103