This post aims to answer all of your HIPAA compliance questions. If you’re just learning about HIPAA compliance, or beginning the process of becoming HIPAA compliant, this article will guide you through the initial steps you must take to adhere to the law. We explain every facet of HIPAA, including information about who needs to be HIPAA compliant, who enforces HIPAA, what happens when you violate HIPAA, and what you must do to become and remain HIPAA compliant.
This is a long, comprehensive post. Explore the full article to gain a holistic understanding of the law or use the table of contents below to find the specific information you need.
Here is what we are going to cover in this post:
I. What is HIPAA Compliance?
The most important thing to remember about HIPAA compliance is that it is an ongoing process. There is no one action, training program, or software that makes your organization HIPAA compliant. To fully obey the law, you must create the necessary documents, including Privacy and Security Policies and Procedures, and follow the protocols for protecting PHI you set. Your HIPAA compliance plan will change as your staff, IT department, and business grows or evolves.
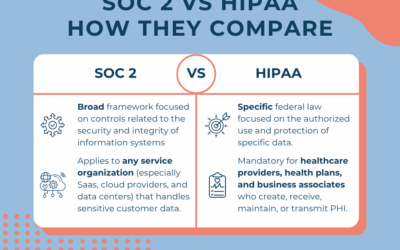
“HIPAA” is the Health Insurance Portability and Accountability Act of 1996. This federal regulation set standards for safeguarding Protected Health Information, or PHI. HIPAA is regulated by the Department of Health and Human Services (HHS) Office of Civil Rights (OCR). HIPAA can also be enforced by State Attorneys General. HIPAA compliance is an ongoing process that requires addressing every facet of this comprehensive law.
A. Protected Health Information (PHI)

HIPAA compliance revolves around keeping Protected Health Information (PHI) safe. PHI is the combination of any health-related information (like a diagnosis or medical record) with a unique personal identifier. Identifiers include: DOB, SSN, physical address, email address, phone number, IP Address, and MAC Address. However, this list is not exhaustive. Any information that ties medical data to a specific person constitutes PHI and must be protected accordingly. Notably, information does not have to be current to qualify. All PHI must be kept for 6 years unless your state has more stringent requirements.
The Privacy Rule and the Security Rule are the two biggest components of the HIPAA law. Each plays a different role in protecting PHI.1
B. The Privacy Rule (2003)
The Privacy Rule establishes guidelines for protecting medical records and other PHI in relation to health plans, health care clearinghouses, and other electronic healthcare communications.
The Privacy Rule requires entities to:
- Appoint a Privacy Officer to oversee the HIPAA Compliance process
- Document Privacy Policies and Procedures
- Sign a Business Associates Agreement with all 3rd party vendors who access PHI on their behalf
- Limits disclosures of PHI without patients’ authorization unless they are required by law
- Allow disclosures pertaining to Treatment, Payment, and Healthcare Operations (TPO)
- Grant patients the right to obtain a list of disclosures, correct their health records, and obtain a copy of their medical information at any time
- Set guidelines for protecting physical PHI2
C. The Security Rule (2005)
The Security Rule regulates cybersecurity and establishes guidelines for protecting electronic PHI (ePHI). The Security Rule uses the National Institute of Standards and Technology Risk Management Framework (NIST-RMF) 800-53 to set guidelines for safeguarding ePHI. The Security Rule establishes administrative, physical, and technical safeguards that entities who come into contact with PHI must implement.3
1. Administrative Safeguards
Administrative safeguards require entities to document the activities they perform for HIPAA compliance. Some of the required activities include:
- Designating a Security Officer (Your Privacy and Security Officer can be the same person)
- Training all staff members who come in contact with PHI
- Completing a thorough Risk Assessment
- Documenting Security Policies and Procedures
- Designating a Security Officer
- Documenting a Disaster Recovery Plan
The Administrative Safeguards are the plans that set the standards for the Physical and Security Guidelines. It’s important to take time to plan for HIPAA compliance first and then implement policies you create. This saves both time and money.
2. Physical Safeguards
Physical safeguards regulate the way entities handle physical systems and equipment that contain PHI. Devices like servers and computers must be kept in a secure location. Any office or building where these devices that contain PHI are stored should have physical security, backup power, and fire suppression systems. Tracking employees’ and vendor access to the building is also a good idea. It’s important to keep detailed access logs of personnel that enter secure onsite spaces to control, monitor, and limit who sees PHI.
If you use a Managed Service Provider or IT contractor, you must have a signed Business Associate or Business Associate Subcontractor Agreement with them.
3. Technical Safeguards
Technical safeguards outline IT-related security practices to protect ePHI. HIPAA requires entities to encrypt data in three phases: at rest, in transit, and in storage. PHI transmitted via email should be sent using email encryption to safeguard the information as it passes from sender to recipient. Only the intended recipient can open an encrypted email, so sensitive information remains safe even when you send it to the wrong person. Examples of technical safeguards include:
- Assigning unique logins for users
- Setting automatic timeouts in systems containing PHI
- Using 2-factor authentication for all systems that hold ePHI
- Installing anti-malware software on devices
- Encrypting hard drives
- Password protecting all devices
- Locking desktop computers to workstations4
II. Who Needs to be HIPAA Compliant?
There are 3 groups that must be HIPAA compliant:
- Covered Entities,
- Business Associates, and
- Business Associate Subcontractors
All of these groups handle PHI on a regular basis and must be equipped to safeguard this sensitive information.
Covered Entities are defined as healthcare providers, health plans, and healthcare clearinghouses. Business Associates are the providers that support Covered Entities, usually IT, lawyers, third party administrators, etc. Business Associate Subcontractors are groups that support Business Associates. For example, a physician practice has hired an IT provider and the IT provider bundles services for the practice. In order to do this, the IT provider will contract with a 3rd party for things like cloud backups. In this case, the Physician would have a BA Agreement with the IT provider, and the IT provider would have BA Subcontractor agreements with their 3rd parties.

III. HITECH Act (2009)
The HITECH Act of 2009 expanded the definition of HIPAA compliance and solidified the fines and penalties for parties who violate the law. The most important changes HITECH brought about include:
- Breach notification rules – requires HHS be notified within 60 days for breaches of 500 or more individuals information
- Allows clients to receive PHI in electronic format
- Established four categories for fines for businesses
- Set penalties for individuals who violate HIPAA
The increase in fines and penalties provided OCR with more resources to investigate and pursue non-compliant entities. From this, we have seen more aggressive action from OCR and State Attorneys General. In the past few years, OCR has made examples of both large and small companies who violate HIPAA. In 2018, we witnessed the biggest fine ever levied for a HIPAA violation in the notorious Anthem breach. However, OCR imposes penalties against small entities too. Last year, a ‘dumpster diver’ retrieved improperly disposed of health records and sold the information on the black market. The breach was discovered and the Covered Entity paid a $100,000 fine even though the company had closed a year prior to the incident.
A. HIPAA Compliance and HITECH: Business Associates
Under HITECH, Business Associates and Business Associate Subcontractors are held to the same HIPAA compliance standards as Covered Entities. This means Business Associates and Subcontractors must also appoint a Privacy and Security Officer, create Privacy and Security Policies and Procedures, sign Business Associate Subcontractor Agreements, and train employees. They are also required to notify Covered Entities they work with of any unauthorized release of PHI.
B. HIPAA Compliance and HITECH: Breaches
Prior to the passage of the HITECH Act, breach notification rules were not as structured. Now, entities must notify individuals within 60 days of the discovery of the breach (if the breach impacted more than 500 people). If the Covered Entity cannot reach 10 or more individuals, they must post a substitute notice to their website or notify local media outlets so they can spread the word of the breach.
However, if the breach impacts fewer than 500 individuals, the entity may document the breach and report it to HHS within 60 days of the end of the calendar year (in which the breach occurred). Note: to achieve HIPAA compliance, entities must always report small breaches, even if they choose to do so at a later date. Some states have stricter breach notification laws; in that case, follow whichever rule is more stringent.5
Lastly, HITECH established four levels of breaches. Each category corresponds with a different punishment based on the severity of the offense. Descriptions of penalties for individuals can be found in the next section.
1. Penalties for Covered Entities
There are both civil and criminal penalties associated with violating HIPAA for individuals and organizations. HIPAA Compliance must be maintained consistently to prevent breaches, or someone will be held liable. The type of breach determines the severity of the penalty. There are four categories:
Type 1 Breach: Did Not Know
We call this the “ignorance is bliss” excuse. The Covered Entity insists they didn’t know there was a problem, and probably would not have known through the exercise of reasonable discretion.
Examples include an unauthorized party monitoring an employee’s cell phone and hackers inserting malware on the server.
Fines start at $100 per HIPAA violation with an annual cap of $25,000 per HIPAA violation.
Type 2 Breach: Reasonable Cause
This is the “I tried, but whoops!” excuse. Despite the company’s best HIPAA compliance efforts, something went wrong or someone made a mistake that caused a HIPAA violation.
Examples include errant fax that triggered a bad outcome and staff overheard talking in an adjacent room when they thought no one could hear.
Fines range from $1,000 – $50,000 per HIPAA violation with an annual cap of $100,000 per HIPAA violation.
Type 3 Breach: Willful Neglect – 60 Days to Correct
The “I can beat the system” excuse. Perhaps the company thought the regulations did not apply to them or simply never got around to implementing a HIPAA compliance program. Maybe they decided to ignore the HIPAA law altogether. Whatever the reason, they were caught. To be classified in this category, the company must correct the HIPAA violation in 60 days and generate a good faith effort to become fully HIPAA compliant.
Fines range from $10,000 – $50,000 per HIPAA violation with an annual cap for $250,000 per HIPAA violation.
Type 4 Breach: Willful Neglect – Not Corrected
This type of HIPAA violation is similar to type 3, however, the company continued to ignore the HIPAA law after the discovery of a breach. They may have been caught by a random audit or a complaint from an individual.
The fines for this are significantly higher indicating that HHS does not take Type 4 HIPAA violations lightly. Each abuse is $50,000 with an annual cap of $1.5 million.
OCR adds an inflation adjustment to all four categories. These adjustments are updated annually.
Notably, breaches have numerous hidden costs, including loss of business, employee trust, and client confidence, especially in the case of large incidents that receive major media attention. The Covered Entity at fault may also incur the cost of legal fees and client protection services, like credit monitoring.
IV. The Omnibus Ruling (2013)
The Omnibus Ruling of 2013 both finalized ideas proposed by the 2009 HITECH Act and added new provisions. Some definitions and guidelines laid out by HITECH were too vague or difficult to understand; the Omnibus Ruling gave concrete meaning to these abstract ideas. Initially, this process was supposed to take about eighteen months. In the end, it took four years to pass this legislation. Most notably, the Omnibus Rule removed the Harm Standard for classifying breaches, established civil penalties for HIPAA violations, altered the rules around marketing, and solidified individuals’ rights to access their information.
Prior to the Omnibus Ruling, breaches were defined by the “Harm Standard.” If an inappropriate disclosure of PHI occurred, it was not considered a breach unless it was proven that it posed a threat to an individual. With the removal of the Harm Standard, breaches are now understood to occur any time PHI is released in an unsecured format, whether or not individuals were hurt by the disclosure or not. Therefore, this change also alters the breach notification rules for Covered Entities; all unauthorized disclosures of PHI must be reported to HHS.
A. Penalties for Individuals
Criminal penalties for non-compliant entities existed years before the Omnibus Ruling established civil penalties for individuals who violate HIPAA law. These punishments include hefty fines and possible jail time. The categories for offenses are as follows:
Level One: Knowingly Obtaining or Disclosing PHI
This is straightforward; stealing and disclosing PHI is punishable with a fine of up to $50,000 and/or imprisonment up to one year.
Level Two: Offenses Committed Under False Pretenses
The type of offense usually describes individuals committing healthcare fraud by posing as another person. If an individual uses someone else’s PHI to pose as them at a financial institution or hospital, they can be fined up to $100,000 and/or imprisoned for up to five years.
Level Three: Offenses Committed with the Intent to Harm an Individual or Profit off of Disclosing Their PHI
A perpetrator falls into this category if they intend to sell, transfer, or use PHI for commercial advantage, personal gain, or harm to another person. This happens often in the case of celebrities; It is not uncommon for hospital staff to sell famous patients’ PHI to the media. Perpetrators are subject to a fine of $250,000 and/or imprisonment for up to ten years.

V. Key HIPAA Compliance Documents
A. Importance of Proper HIPAA Compliance Documentation
HIPAA requires specific documentation which you must have in order to be fully compliant with the law. When HHS conducts audits, they look for current and historical HIPAA compliance. Create, maintain, and regularly update (annually) the following documents. By doing so, you will have a written record of your HIPAA compliance plan which you may refer back to. This is vital for implementation and surviving an audit from health insurance carriers or HHS.
B. Risk Assessment Document for HIPAA Compliance
A Risk Assessment (sometimes referred to as a Risk Analysis) is the first document you should complete when you begin forming your HIPAA compliance plan. The Risk Assessment (RA) is full of detailed questions about your organization. When completed, it provides a comprehensive view of what your organization does correctly and what you need to work on. It also prioritizes the tasks you must complete first to best secure your organization. The RA identifies all potential vulnerabilities that must be addressed and it needs to be reviewed annually. It is recommended that you perform a RA from scratch every 2-3 years, or when you have a significant change in processes, IT environment, and/or staff.
C. Privacy Policies & Procedures Document for HIPAA Compliance
Privacy Policies and Procedures are the detailed plans a group creates for becoming HIPAA compliant. This document contains information about how the company manages the PHI it comes into contact with, who the Privacy Officer is and what their duties are, how noncompliant employees and Business Associates will be sanctioned, and more. It explicitly states how the company manages to safeguard PHI in even the most mundane daily tasks, like sending and receiving faxes.
D. Security Policies & Procedures Document for HIPAA Compliance
Security Policies and Procedures are a separate document that accompanies the Privacy Policies and Procedures. It goes into detail about the technological measures Covered Entities, Business Associates, and Subcontractors take to protect ePHI for HIPAA compliance. This document includes plans for anti-malware software, encryption policies, screening for new workforce members or vendors, managing data sources, and electronic access control policy. Everyone in the company that handles PHI must be trained on the Privacy and Security Policies and Procedures. If staff members don’t know or don’t understand the Policies, the company may as well not have them. This is a crucial part of HIPAA compliance.
E. Business Associates Agreement Document for HIPAA Compliance
A Business Associate Agreement (BAA)/Business Associate Subcontractor Agreement (BASA) is a required document designed to protect both parties in a partnership. If a Covered Entity’s vendors or contractors see any PHI on their behalf, there must be a signed BAA/BASA in place. This document is required to maintain HIPAA compliance. Without a signed BAA/BASA, Covered Entities can be held liable for their Business Associates or Subcontractors’ mistakes in the event of a breach. Business Associates must have a Business Associate Subcontractor Agreement with companies they partner with. A strong BAA/BASA should include the following information:
- Descriptions of permitted and required PHI use by the Business Associate/Subcontractor
- Requirements for the Business Associate/Subcontractor to implement appropriate safeguards necessary to protect the Covered Entity’s PHI
- Agreement that the Business Associate/Subcontractor will not use or further disclose the Covered Entity’s PHI
- Guidelines for permitted uses and disclosures of PHI on behalf of the Covered Entity
- Breach notification obligations
- Process for terminating the business relationship between the Covered Entity and the Business Associate/Subcontractor
F. BYOD (Bring Your Own Device) Policy Document for HIPAA Compliance
This document may not be applicable to all Covered Entities. However, it is absolutely necessary in workplaces that allow employees to use personal devices (cell phones, laptops, tablets) to connect to networks or systems that access PHI. A BYOD Policy outlines all of your organization’s rules for employees devices. A good BYOD should include the following stipulations:
- Requirement that the device must be configured by the company’s IT department
- Agreement to have the device remotely wiped if it is lost or stolen
- A password policy, including rules for how often passwords must be changed
- Reimbursement for person device use, if the company offers to their employees
- Acceptable personal device usage in the workplace, including a list of websites or apps employees should not use during business hours
- Agreement to allow IT to program the device
G. Notice of Privacy Practices
A Notice of Privacy Practices (NPP) publicly states, in plain language, how Covered Entities plan to handle PHI in order to stay HIPAA compliant. A copy of this document must be provided to all clients or employees who share PHI with the company at least once annually or at times of renewal in coverage. Business Associates do not need to provide an NPP unless their company offers a group health plan to 50+ individuals.
H. Audit Logs Document for HIPAA Compliance
Logs are a critical – not to mention required – way for organizations to monitor network activity. In the event of a breach, audit logs will help you understand what went wrong and who is responsible, so you can mitigate the incident as quickly as possible. In any audit, whether random or due to an incident, HHS will want to see these logs. Like all HIPAA compliance documentation, logs must be kept for six years, unless state requirements are more stringent. Logs should include this information – and we recommend making a separate log for each of these things:
- User log in
- Changes to databases
- New users added
- User access levels
- Files accessed by users
- Changes to operating systems
- Status of firewall programs
- Status of anti-malware programs6
VI. How Do I Become HIPAA Compliant?
As mentioned before, HIPAA compliance is an ongoing process. Think of it as a constant effort you must maintain rather than an accomplishment that you achieve.
The first step towards HIPAA compliance is creating the necessary documentation. Begin with a Risk Assessment. This document, which is required by HIPAA, highlights all of your organization’s potential vulnerabilities that need to be addressed. It will also inform the creation of your Privacy and Security Policies and Procedures. Your Policies and Procedures documents provide information about how your organization will protect PHI in all its forms – oral, written, and electronic.
In this process, name a Privacy Officer (PO) and Information Security Officer (ISO) (this may be the same person in small organizations) to oversee all HIPAA compliance efforts and enforcement. The PO and ISO may be managers, HR personnel, company owners, or anyone with the authority to enforce organization-wide HIPAA compliance.
Once you have created these documents, train your staff and your Policies and Procedures and their role in maintaining HIPAA compliance. Employees must be retrained annually.
If your organization works with any third party vendors or organizations that access PHI on your behalf, have a signed Business Associate Agreement with them to ensure that they are doing everything possible to protect your sensitive data. The ultimate goal is to protect PHI at all times, in all its forms.
VII. What is a HIPAA Breach?
In the simplest terms, a breach is a HIPAA violation; it is essentially a HIPAA compliance failure. A breach occurs any time an individual’s PHI is released in an unsecured format. HHS recently removed the “Harm Standard” from the Omnibus Ruling (a 2013 update to HIPAA), which now means that any instance of an unauthorized third party accessing, using, acquiring, or disclosing PHI constitutes a breach. All incidents are presumed to be breaches unless proven otherwise.
Breach examples:
- An employee of a medical facility leaves their unencrypted laptop containing a database of all patient information in their car and someone steals it.
- An administrator at a health insurance agency accidentally faxes a document containing PHI to the wrong number.
- A hacker gains access to PHI by installing malware on a Covered Entity’s network.
A. What Happens When a Breach Occurs?
When a breach occurs, an organization’s HIPAA compliance team must follow three steps:
1. Perform a Risk Analysis
This process is required by HIPAA. It allows the Covered Entities, Business Associates, and Subcontractors to understand the full impact of the breach so they can properly mitigate it.
2. Contact the Authorities
If the breach impacted more than 500, HHS (and in some states the state attorney general’s office) must be notified.(Check with your state’s breach rules for breach reporting rules and time frames.) If the breach impacted fewer than 500 people, the Covered Entity, Business Associate, or Subcontractor can either report to HHS right away or document the breach and report all of the small breaches within 60 days of the end of the calendar year.
3. Notify Individuals
HIPAA’s Breach Notification Rule requires Covered Entities to alert individuals no later than 60 days after the discovery, or when the Covered Entity should have known about the breach. If the Covered Entity is not able to reach 10 or more individuals, they must either post the breach notice on the home page of its web site for a minimum of 90 days or notify major print or broadcast media where the affected individuals likely reside. The covered entity must also include a toll-free phone number that remains active for at least 90 days where individuals can learn if their information was involved in the breach.7
If the incident involved more than 500 people, the Covered Entity must also alert the media. Covered Entities can report small (under 500 individuals) breaches to HHS immediately or annually. Note: Some states have breach notification laws that are more stringent than HIPAA. If your state’s regulation is more strict, you must follow that, but the HHS notification rules still must be followed.
VIII. Who Enforces HIPAA Compliance?
The US Department of Health and Human Services (HHS) Office of Civil Rights (OCR) enforces HIPAA. Additionally, individual State Attorney Generals have the right to levy fines and penalties against entities that violate HIPAA.
A number of state Supreme Courts Connecticut, Indiana, Massachusetts, Missouri, North Carolina, Vermont, and West Virginia upheld HIPAA as a standard of care in one or more rulings. This means that individuals can sue providers, carriers, and employers for breaches of their health records. In the eyes of these courts, breaches are a failure (on behalf of the providers, carriers, or employers) to uphold their patients’ privacy standards set forth by HIPAA.
IX. Conclusion
Remember, HIPAA compliance is that it is an ongoing process. There is no one action, training program, software, or one-step solution that makes your organization HIPAA compliant. To fully obey this law, you must create the necessary documents and train employees to follow the protocols for protecting PHI you set. This HIPAA compliance process is not quick or easy, but it does protect your business from the serious damage done by breaches.
Our HIPAA compliance services help ensure that your business follows the basic HIPAA rules and guidelines to protect sensitive patient information. Our team of experts is dedicated to providing affordable rates and personalized solutions to help you become HIPAA compliant. We understand that navigating the complex requirements of HIPAA can be challenging, which is why we offer a comprehensive range of services to meet your unique needs. From risk assessments to employee training, we have the tools and expertise necessary to help your business achieve and maintain HIPAA compliance. Contact us today to learn more about how we can help you protect your patients, your employees, and your business.
Sources
- https://www.hhs.gov/hipaa/for-professionals/security/laws-regulations/index.html
- https://www.hhs.gov/hipaa/for-professionals/privacy/index.html
- https://www.hhs.gov/hipaa/for-professionals/security/index.html
- https://www.hhs.gov/hipaa/for-professionals/security/laws-regulations/index.html
- https://www.hhs.gov/hipaa/for-professionals/special-topics/hitech-act-enforcement-interim-final-rule/index.html
- https://www.hhs.gov/hipaa/for-professionals/covered-entities/sample-business-associate-agreement-provisions/index.html
- https://www.hhs.gov/hipaa/for-professionals/breach-notification/index.html